Configuring Active Directory Federated Services (ADFS) for SSO Learner Authentication
Table of Contents
- Add a Relying Party Trust for Infosec IQ
- Edit Claim Rules for Relying Trust Party you created
- Test Metadata URL in Infosec IQ
- IDP Initiated Training
System Requirements: In order to successfully validate our metadata, you must have TLS 1.2 enabled on your ADFS Server. After enabling, also confirm that you have the 4.6.2 version of .NET framework installed as TLS 1.2 requires it.
Before creating the relying party trust application in ADFS, you will need to obtain Infosec IQ’s Metadata URL. To do so:
- Login to Infosec IQ
- Navigate to the settings gear in the top right corner and select Learner Authentication (SSO)
- In the Sign sign-on section, select setup
- Do not adjust any of the settings and click save in the bottom right-hand corner. This will expose the SP Metadata, Entity ID, and ACS URLs for your organization. You will need these URLs to perform the below configuration steps
Add a Relying Party Trust for Infosec IQ
- Open up ADFS Management.
- Select Add Relying Party Trust.

- When the Relying Party Trust Wizard opens up select Start.
- Select the option Import data about the relying party published online or on a local network and the correct metadata URL.
- Leave the Display name as is and click Next.
- Select I don’t want to configure multi-factor authentication settings for this relying party trust at this time and click next.
- Select Permit all users to access this relying party and click Next.
- In the Ready to Add Trust step click Next.
- Leave the box checked to open the edit claims rule dialog… and close window.
Edit Claim Rules for Relying Trust Party you created
Part 1
-
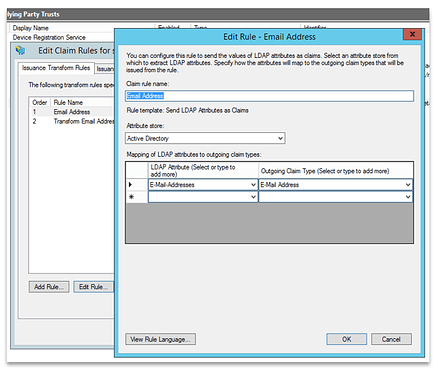
In the edit claims run window select Add Rule.
-
Use the Send LDAP Attributes as Claims template and click Next.
-
Update the following sections (please note: these must be selected from the dropdown menu and not typed in):
- Claim rule name: Email Address
- Attribute Store: Active Directory
- LDAP Attribute: E-Mail-addresses
-
Outgoing Claim Type: E-Mail Address
-
Click Finish after completing the above fields.
Part 2
-
Stay in the edit claims run window to add another rule.
-
Used to Transform an Incoming Claim template and click Next.
-
Update the following sections (please note: these must be selected from the dropdown menu and not typed in):
- Claim Rule Name: Transform Email Address
- Incoming Claim Type: E-Mail Address
- Outgoing Claim Type: Name ID
- Outgoing name ID Format: Email
-
Select Pass through all claim values
-
Click Ok and close the claims window.
Test Metadata URL in Infosec IQ
This will be your Metadata URL:
https://[insert ADFS Domain Name]/FederationMetadata/2007-06/FederationMetadata.xml
- Login to Infosec IQ
- Navigate to the settings gear (top-right corner) and select Learner Authentication (SSO) from the drop-down menu
- In the Single sign-on section, select setup
- Paste the above, modified, Metadata URL into the IdP Metadata URL box
- (Optional) If you are planning configuring IdP initiated training (see next section for configuration steps), make sure the iDP-initiated SSO toggle under settings is enabled.
- Click Save
- Once saved, you can perform a test by expanding the Actions dropdown menu and clicking test. Follow the prompts on the screen to complete the test. If your test isn’t successful, please contact support for further assistance.
- After the test is successful, the SSO configuration will be active for all users
IDP Initiated Training
IDP Initiated Training is a way for Admins to share a universal training link to all their learners. This link will need to be obtained from ADFS. Follow the below steps:- Navigate to your ADFS Server and open ADFS Management
- Click on the relying party trust that you configured for Infosec IQ and select Edit Claim Rules
- Navigate to the Issuance Authorization Rules tab and confirm that all users are permitted to access the relying party trust
- If All Users didn’t have permission click Apply and ok
Steps 4-7 will cover how to gather the information that will be needed to complete the following URL:
https://[ADFS Domain Name]/adfs/ls/idpinitiatedsignon.aspx?LoginToRP=[RelayingPartyIdentifier]
- To obtain the Relying Party Identifier, Right-click on the Relying Party Trust and select Properties
- Click on the Identifiers tab and copy the information listed under the Relying Party Identifiers section
- Add the relying party identifier and your ADFS Domain Name to the URL:
https://[ADFS-DomainName]/adfs/ls/idpinitiatedsignon.aspx?LoginToRP=[RelayingPartyIdentifier] - Once the above link has been modified, it can now be shared with your learners.
Note: We recommend testing this link with a few learners before sending it out to everyone. To do this, enroll your test group in an AwareEd campaign with Learner Authentication enabled.